Can someone hack my iPhone? Yes, someone can hack your iPhone. Although iPhones are secure, vulnerabilities still exist.
IPhones are renowned for their robust security features. Apple regularly updates its software to protect users from potential threats. Despite these measures, hackers continuously find new ways to exploit security loopholes. Common hacking methods include phishing attacks, malicious apps, and exploiting outdated software.
Users should remain vigilant by keeping their devices updated and avoiding suspicious links or downloads. Strong passwords and two-factor authentication add extra layers of security. Regularly monitoring your device for unusual activity can also help in early detection of any breaches. While no device is entirely hack-proof, taking these precautions significantly reduces the risk of your iPhone being compromised.
Can Someone Hack My iPhone?

The Fortress Of Ios Security
Apple’s iOS is renowned for its robust security features. Many users wonder, “Can someone hack my iPhone?” This post dives into the security measures that make iOS a fortress against hacking attempts. By understanding these features, you can better protect your device.
Apple’s Security Measures
Apple implements multiple layers of security to safeguard iPhones. These include:
- Encryption: iOS encrypts data to prevent unauthorized access.
- App Store Review: Apple reviews all apps to ensure they are safe.
- Two-Factor Authentication: Adds an extra layer of security to your Apple ID.
- Regular Updates: Frequent updates fix security vulnerabilities.
These measures create a secure environment for iPhone users.
Ios Vs. Other Operating Systems
Comparing iOS to other operating systems reveals key differences in security:
| Feature | iOS | Android |
|---|---|---|
| App Review Process | Strict | Less Strict |
| Software Updates | Frequent | Varies by Manufacturer |
| Encryption | Enabled by Default | Varies |
| Malware Protection | Strong | Varies |
iOS stands out due to its stringent app review process and frequent updates. These factors make it harder for hackers to exploit iPhone users.
Myth Vs. Reality: Iphone Vulnerabilities
Many believe iPhones are immune to hacking. This belief is partly true. iPhones have strong security features. But, they are not invincible. Let’s uncover the truth behind iPhone vulnerabilities.
Common Misconceptions
Many users think iPhones can’t be hacked. This is a misconception. No device is completely secure. Here are some common myths:
- Myth: iPhones are unhackable.
- Myth: Only Android phones get malware.
- Myth: iOS updates always fix all bugs.
These myths make users less cautious. Always stay vigilant. Understand the reality of iPhone security.
Documented Security Flaws
Apple works hard to secure iPhones. Yet, some flaws have been found. Here are some documented security issues:
| Flaw | Description |
|---|---|
| Zero-day exploits | Hackers find and use unknown flaws. |
| Jailbreaking | This bypasses security to gain full control. |
| Phishing attacks | Trick users into giving personal info. |
These flaws show iPhones can be at risk. Always update your iPhone. Use strong passwords and avoid suspicious links.
High-profile Hacking Incidents
iPhones are popular devices. But they are not immune to hacking. Some high-profile cases have shocked the world. Below are two major incidents.
Celebrity Icloud Breaches
Celebrities store personal photos in iCloud. Hackers have targeted these accounts. In 2014, many private photos were leaked. This event was known as “The Fappening.” Hackers used phishing emails to steal iCloud passwords. Famous people like Jennifer Lawrence were affected.
This breach showed the dangers of weak passwords. It also highlighted the importance of two-factor authentication. Always use strong passwords and enable two-factor authentication.
Governmental Intrusions
Government agencies can also hack iPhones. In 2016, the FBI wanted to unlock an iPhone. This phone belonged to a suspect in a crime. Apple refused to help. The FBI then found a third party to unlock the phone. This event raised questions about privacy and security.
Governments may use advanced tools. These tools can bypass iPhone security. Always keep your software updated. This helps protect against new threats.
Malware And Iphone: A Rare Encounter
Many people ask, “Can someone hack my iPhone?” The answer is complex. iPhones are generally secure. Apple’s iOS system has strong protections. Yet, malware can still pose a threat. It’s rare but it happens.
Types Of Malware On Ios
Malware on iPhones comes in various forms. Here are some common types:
- Spyware: Tracks your activities and steals data.
- Adware: Bombards you with unwanted ads.
- Trojans: Disguises as legitimate apps to access your data.
Prevalence And Impact
Malware on iPhones is rare but impactful. iOS’s closed ecosystem limits malware spread. Yet, jailbroken iPhones are more vulnerable.
| Malware Type | Impact |
|---|---|
| Spyware | Data theft, privacy invasion |
| Adware | Annoying ads, slow performance |
| Trojans | Data access, hidden activities |
Even though malware is rare, it can be harmful. Always update your iPhone. Stick to trusted sources for apps.
Phishing Attacks: The Human Weakness
Phishing attacks are one of the most common ways hackers target iPhones. These attacks exploit human weaknesses rather than technical vulnerabilities. Hackers use deceptive messages to trick users into revealing sensitive information. This makes it crucial to understand and recognize phishing attempts.
Spotting Phishing Attempts
Knowing how to spot phishing attempts can protect your iPhone from hackers. Here are some key signs:
- Suspicious emails or messages: Look out for emails from unknown sources.
- Urgent requests: Be cautious of messages asking for urgent action.
- Misspelled URLs: Always check the URL for any spelling errors.
- Attachments and links: Avoid clicking on unknown attachments or links.
Protecting Yourself From Phishing
Taking proactive steps can help you protect yourself from phishing attacks. Follow these tips:
- Enable two-factor authentication: Add an extra layer of security to your accounts.
- Use a spam filter: Ensure your email provider has a strong spam filter.
- Verify the sender: Always verify the sender’s email address.
- Educate yourself: Stay informed about the latest phishing techniques.
By understanding and recognizing phishing attempts, you can safeguard your iPhone against hackers.

Physical Security: Losing Your Iphone
Losing your iPhone is more than an inconvenience. It can lead to serious security risks. Thieves can access your personal data and sensitive information. Understanding these risks and knowing the steps to take is crucial.
Stolen Iphone Risks
- Personal Data Exposure: Thieves can access photos, messages, and emails.
- Financial Information: Banking apps and saved passwords are at risk.
- Identity Theft: Hackers can misuse your personal information.
- Social Media Breach: Unauthorized access to your social media accounts.
Steps To Take When Iphone Is Lost
- Use Find My iPhone: Log in to iCloud and locate your device.
- Enable Lost Mode: Lock your iPhone remotely and display a contact number.
- Report to Authorities: File a report with local law enforcement.
- Change Passwords: Update passwords for iCloud, email, and banking apps.
- Notify Your Carrier: Inform your carrier to disable your SIM card.
| Action | Purpose |
|---|---|
| Use Find My iPhone | Locate and protect your device. |
| Enable Lost Mode | Lock your iPhone and display a contact number. |
| Report to Authorities | File a report with local law enforcement. |
| Change Passwords | Update passwords for iCloud, email, and banking apps. |
| Notify Your Carrier | Disable your SIM card to prevent misuse. |
App Store: The Gatekeeper
The App Store is the gatekeeper for your iPhone. It ensures all apps are safe. Apple has strict rules for apps. These rules aim to protect users. But can someone hack your iPhone through apps? Let’s explore.
App Review Process
Apple uses a strong app review process. Each app goes through many checks. The review team looks for malware. They also check for privacy issues. This process makes the App Store safe.
| Step | Description |
|---|---|
| Submission | Developers submit their apps to Apple. |
| Review | Apple’s team reviews the app for safety. |
| Approval | Safe apps get approved and listed. |
Rogue Apps: Slip Through The Cracks?
Sometimes, rogue apps can slip through. These apps may have hidden malware. They can steal your data. But Apple removes them quickly. They also notify users who downloaded them.
- Rogue apps can steal data.
- Apple quickly removes them.
- Users get notified if they downloaded any.
Stay safe by downloading apps only from the App Store. Always read reviews and permissions. Keep your iPhone updated with the latest iOS.
Ios Updates: Patches And Protections
Keeping your iPhone safe is crucial. One of the key ways Apple protects your device is through regular iOS updates. These updates not only bring new features but also vital security patches. Understanding why these updates are important can help you keep your iPhone secure from potential hackers.
Importance Of Regular Updates
Regular updates are essential for your iPhone’s security. Apple releases updates to fix vulnerabilities that hackers might exploit. Skipping these updates leaves your device exposed to risks. Always ensure your iPhone is running the latest iOS version.
Here are some reasons why regular updates are crucial:
- Security Patches: Fixes for known vulnerabilities.
- Performance Enhancements: Improvements in speed and responsiveness.
- Bug Fixes: Resolves minor issues affecting user experience.
- New Features: Adds new functionalities to your iPhone.
Update-related Security Enhancements
Each iOS update includes specific security enhancements. These are designed to protect your data and privacy. Some of these enhancements include:
- Encryption Improvements: Strengthens data encryption to prevent unauthorized access.
- App Permissions: Controls which apps can access sensitive information.
- Two-Factor Authentication: Adds an extra layer of security to your Apple ID.
- Malware Protection: Detects and removes malicious software.
Apple continually works to enhance iPhone security. Each update makes it harder for hackers to infiltrate your device. Here’s a quick look at the latest iOS update features:
| iOS Version | Key Security Features |
|---|---|
| iOS 15 | Enhanced privacy settings, App Tracking Transparency |
| iOS 16 | Advanced data encryption, Improved Face ID |
Ensure you enable automatic updates on your iPhone. This way, you won’t miss critical security patches. Regular updates are a small step that provides substantial protection.
Securing Your Iphone: Best Practices
Many users worry about their iPhone’s security. Taking some simple steps can help keep your data safe. Below are some best practices to secure your iPhone.
Setting Strong Passwords
A strong password is your first line of defense. Avoid using simple passwords like “123456” or “password”. Instead, create a unique and complex password.
Follow these tips to set a strong password:
- Use at least 12 characters.
- Include uppercase and lowercase letters.
- Add numbers and special characters.
- Avoid using personal information like your name or birthdate.
Enabling Two-factor Authentication
Two-Factor Authentication (2FA) adds an extra layer of security. Even if someone knows your password, 2FA will protect your account.
To enable 2FA, follow these steps:
- Go to Settings on your iPhone.
- Tap on your name at the top.
- Choose Password & Security.
- Select Two-Factor Authentication and follow the instructions.
With 2FA, you will receive a code on your trusted device. Enter this code to access your account.
When Hacking Happens: Recovery Steps
Finding out that your iPhone has been hacked can be scary. To get back control, follow these recovery steps. This guide will help you minimize damage and secure your device.
Damage Control
Act quickly to limit the damage. The first step is to change your passwords. This includes your Apple ID, email, and any important apps.
Next, check for unauthorized apps. Remove any apps that you did not install. Look for suspicious activity in your accounts.
Enable Two-Factor Authentication (2FA) on your Apple ID. This adds an extra layer of security. You will need your phone and another device to log in.
Reset your iPhone to factory settings if needed. Go to Settings > General > Reset > Erase All Content and Settings. This will delete all data, so backup your important files first.
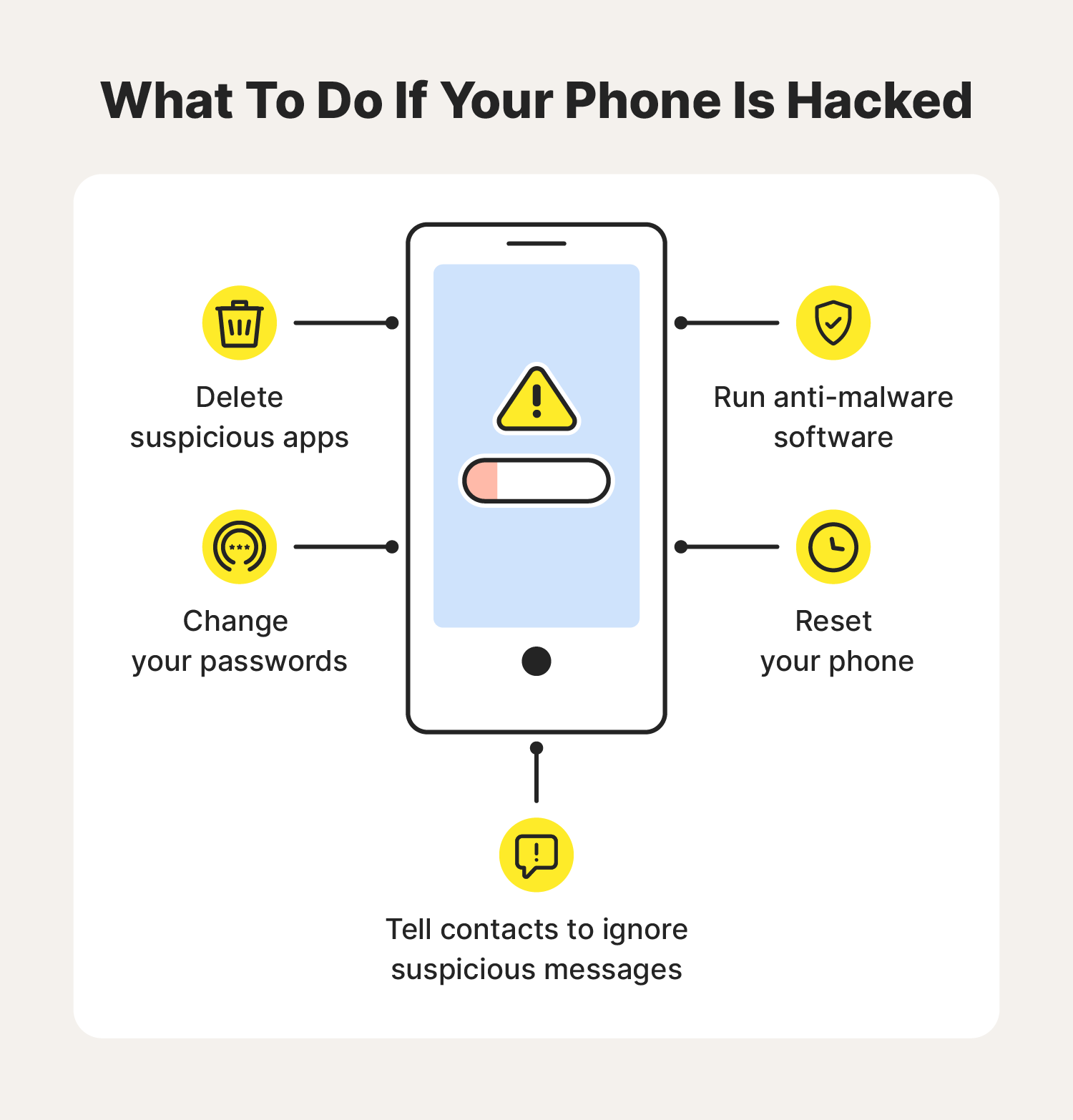
Reporting And Rectifying
Report the hack to Apple Support. They can help you secure your account.
- Visit the Apple Support website.
- Explain the situation in detail.
- Follow their instructions carefully.
Inform your contacts about the hack. They should be aware if they receive strange messages from you.
Check your financial accounts for unusual activity. Inform your bank if you notice anything suspicious. They can help protect your accounts.
Install antivirus software on your iPhone. It can help detect and remove malware. Keep your software updated to protect against new threats.
| Step | Action |
|---|---|
| 1 | Change passwords |
| 2 | Check for unauthorized apps |
| 3 | Enable Two-Factor Authentication |
| 4 | Reset your iPhone |
| 5 | Report to Apple Support |
| 6 | Inform your contacts |
| 7 | Check financial accounts |
| 8 | Install antivirus software |
Follow these steps to recover from an iPhone hack. Stay vigilant to keep your device secure.
Conclusion
Protecting your iPhone from hackers is essential. Regular updates and strong passwords can enhance security. Be cautious of suspicious links and apps. Stay informed about potential threats. By taking these steps, you can significantly reduce the risk of hacking. Keep your iPhone safe and secure with these practices.




